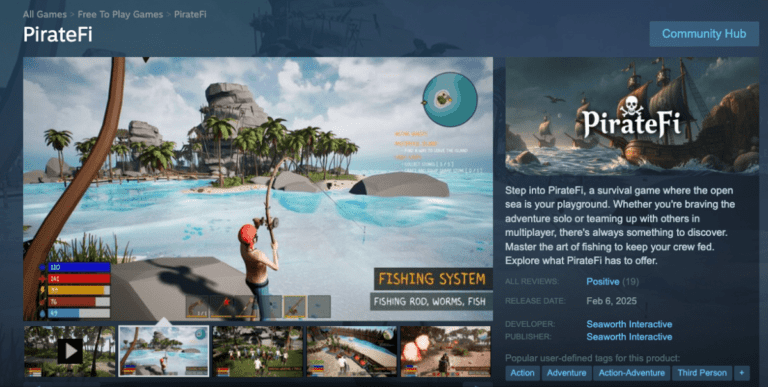
Last week, Valve removed a game from Steam Steam’s electronics because the product was tied with malicious software.
After removing the game, called Piratefi, security researchers analyzed malware and found that anyone who planted it amended an existing video game in an attempt to overcome the players to install an info-steealer called Vidar.
Marius Genheimer, a researcher who analyzed malicious software and working on the Secuinfra Falcon team, told TechCrunch that judging by the command and control servers related to malware and its configuration: massively. ”
“It is very likely that it was never a legal, running game that changed after the first publication,” Genheimer said.
In other words, Piratefi was designed to spread malware.
Genheimer and his colleagues also found that Piratefi was built with modification an existing game standard It’s called Easy Survival RPG, which is priced as a game creation application that “gives you everything you need to develop your own singleplayer or multiplayer”. The toy manufacturer costs between $ 399 and $ 1,099 on the license.
This explains how hackers were able to send a functional video game with their malicious software with little effort.
According to Genheimer, malware Vidar Infostealing is able to steal and eliminate various types of data from the computers it includes, including: Passwords from the Web Browser Function, Cookies Session that can be used to connect as someone Without needing their password, tissue browser history, wallet details encryption, screenshots and two -factor codes by specific symbols generators, as well as other files on a person’s computer.
Vidar has been used in various hacking campaigns, including Someone trying to steal The Booking.com Hotel credentials, others aimed at Ransomware developmentand another attempt for installing malicious ads to Google search results. During 2024, the Cyberspace Coordination Center (HC3) referenced This Vidar, first discovered in 2018, “has grown up as one of the most successful infostealers”.
Infostealers are common types of malware designed to steal information and data from a victim’s computer. Infostealers are often sold in the Malware-A-A-Service model, which means that malware can be purchased and even used by hackers with few skills. This also makes the determination of who was behind the Piratefi “very difficult”, Genheimer said, as Vidar “is widely adopted by many cyberspace”.
Contact us
Do you have more information about this malicious software or other video -related halls? From a device and non-work network, you can contact Lorenzo Franceschi-bicchierai safely on the mark on +1 917 257 1382, or through the telegram and keybase @lorenzofb or email. You can also contact TechCrunch via securedrop.
Genheimer said they analyzed various samples of malicious software included in Piratefi, one found in the online repository Malware Virustotal, which was Apparently uploaded by a player in Russia; Another one found through Steamdb, a website that publishes information on the games hosted in Steam. Researchers found another sample in an Intelligence database that they have access to. All three samples of malware have the same functionality, according to Genheimer.
The valve did not respond to TechCrunch’s request for comments.
Seaworth Interactive, its alleged developers PirateIt has no apparent presence on the internet. Until last week, the game had Account xthat has now been removed. The account included a link to the game in Steam.
The account owners did not respond to a request to chat through a direct message before it was removed.