Consumer spyware applications that are constantly watching and watching private messages, photos, phone calls and real -time location are a constant problem for Android users.
This guide can help you identify and remove common tracking apps from your Android phone, such as Thetruthspy, Cocospy and Spyic, among others.
Consumer spyware applications are often sold on the pretext of monitoring children or family monitoring software, but referred to as “stalkerware” and “spouseware” for their ability to monitor and attend partners or spouses without their consent. These spyware apps are downloaded from the exterior of the Google Play App Store, planted on a person without permission and often disappear from the home screen to avoid detection.
Stalkerware applications are based on the abuse of the built -in Android features commonly used by companies to manage their employees’ work phones or to use the Android accessibility function to snoop on someone’s device.
You may notice that your phone is acting unusually, running warmer or slower than usual or using large amounts of network data, even when you are not actively using it.
The check to determine if your Android device is compromised can be done quickly and easily.
Before you start
It is important to have a security plan and reliable support if you need it. Keep in mind that removing the spyware software from your phone can alert the person who put it in, which could create an unsafe situation. THE Coalition against Stalkerware It offers tips and guidance for Stalkerware victims and survivors.
Note that this guide only helps you to locate and remove spyware applications, does not delete the data already collected and uploaded to its servers. Also, some versions of Android may have slightly different menu options. As is standard with any advice, follow these steps at your own risk.
Make sure Google Play Protect is on
Google Play Protect is one of the best safeguards to protect against malicious Android applications by viewing applications obtained from Google Applications store and external sources for potentially malicious activity. These protections stop working when the play Protect is off. It is important to ensure that Play Protect is enabled to ensure that it works and scans for malicious applications.
You can check that Play Protect is enabled through the Play Store app settings. You can also scan for harmful applications if a scan has not already been done.
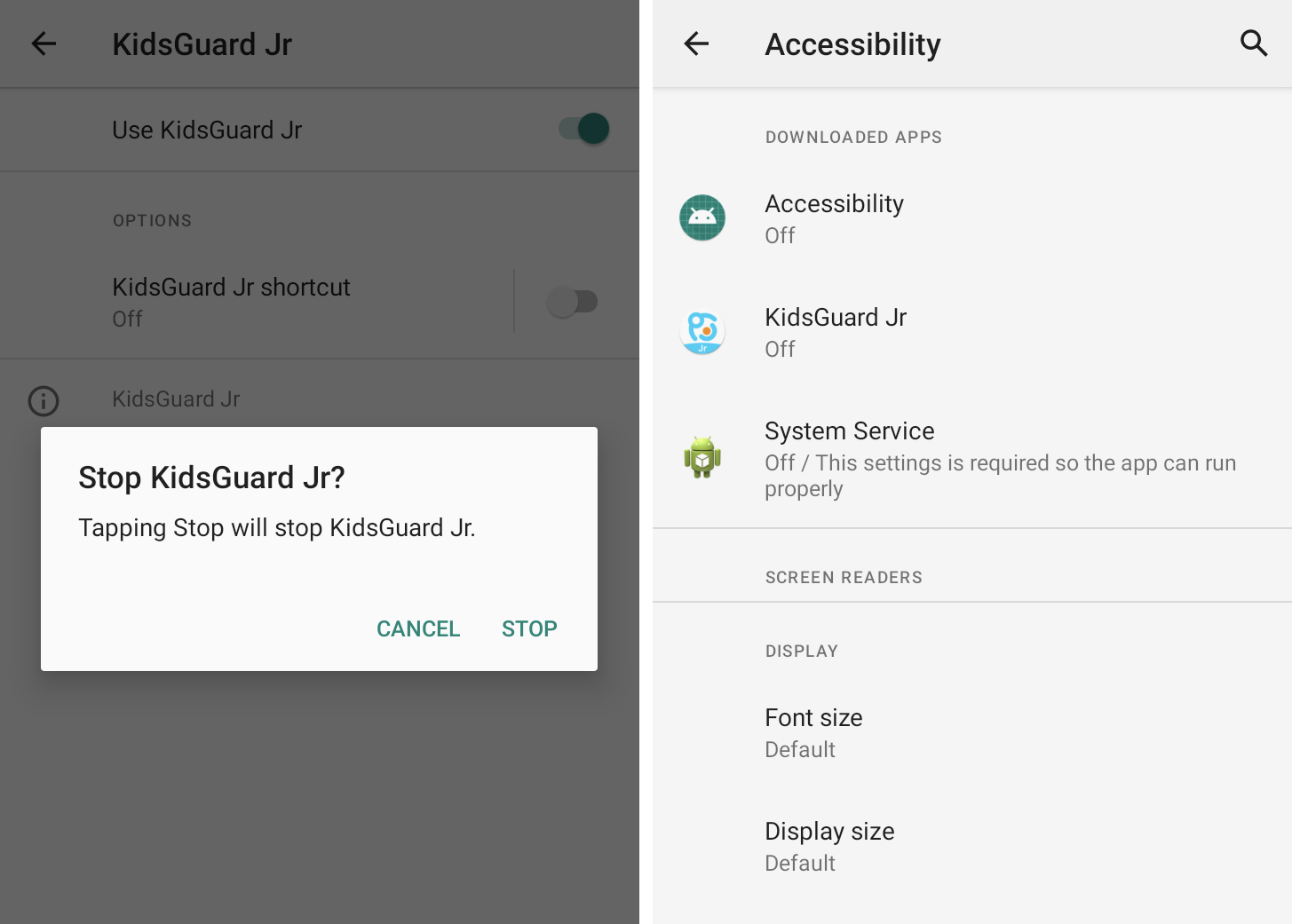
Check if accessibility services have changed
Stalkerware is based on deep access to your device to access data and is known to have abused Android accessibility function, which, by design, requires broader access to the operating system and your data readers and other accessibility functions.
Android users who do not use applications or accessibility capabilities should not see applications in this section of Android settings.
If you do not recognize a download service in accessibility options, you may want to disable it in the settings and remove the application. Some Stalkerware applications are disguised as ordinary applications that seek and are often called “Accessibility”, “Health of Devices”, “System Service” or other harmless names.

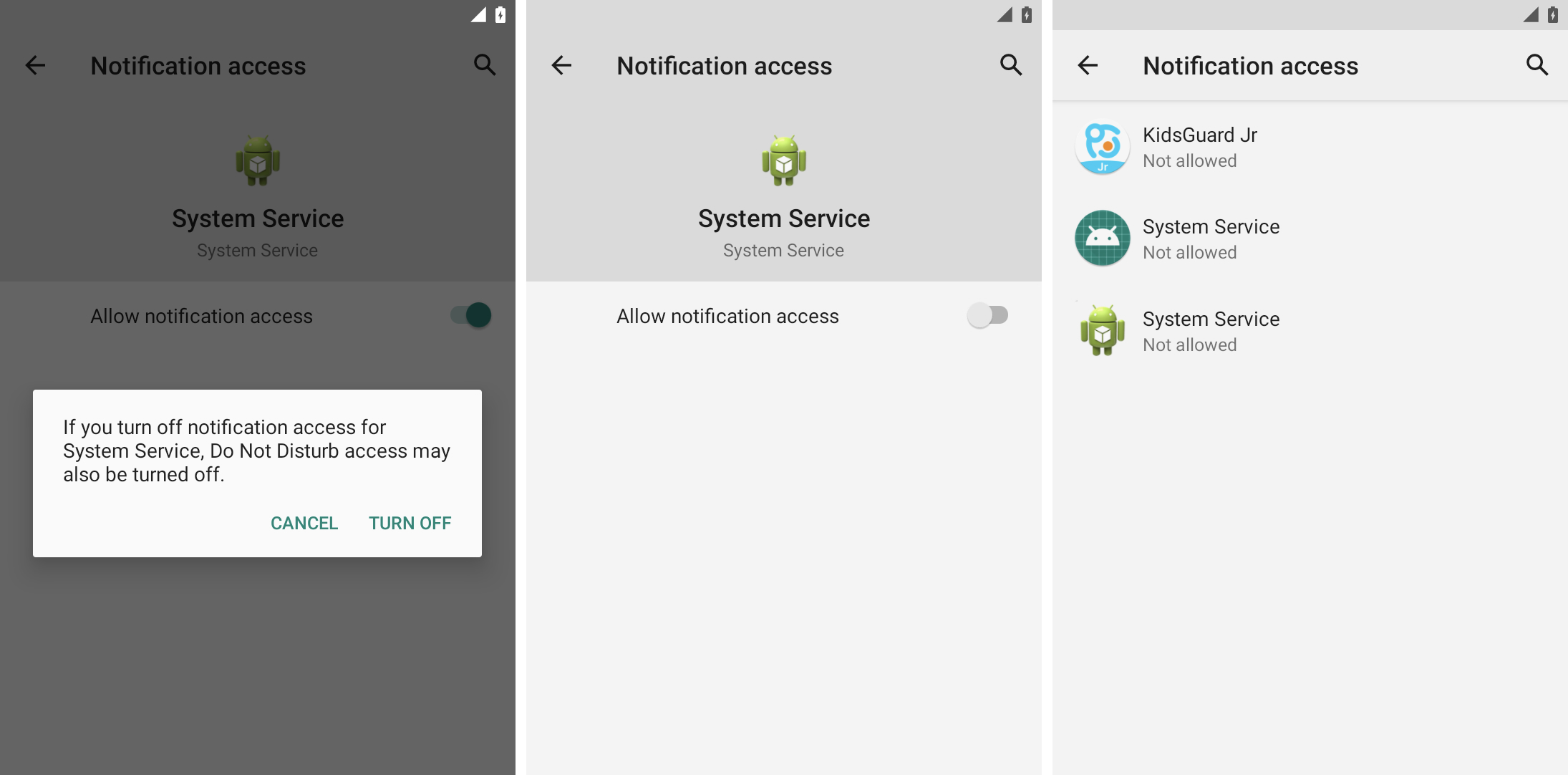
Check any application access to notifications
Like accessibility features, Android also allows third -party applications to access and read your incoming alerts, as they allow smart speakers to read your alerts loudly or your car display notifications in the control panel. Alert access to a Stalkerware application allows for persistent surveillance of your notifications, which includes the content of messages and other notifications.
You can check which applications have access to your alerts by checking Android Alerts Access Settings under special access to the application. Some of these applications can be recognized, such as Android Auto. You can turn off the notice access for any application that you do not recognize.

Check if a device administrator app has been installed
Other features usually abused by stalkerware are Android Device Management options, which have similar and even wider access to Android devices and users’ data.
Device management options are commonly used by companies to manage their employees’ phones, such as wiping the phone in the event of the theft to prevent data loss. But these features also allow stalkerware to snoop on the Android screen and device data.
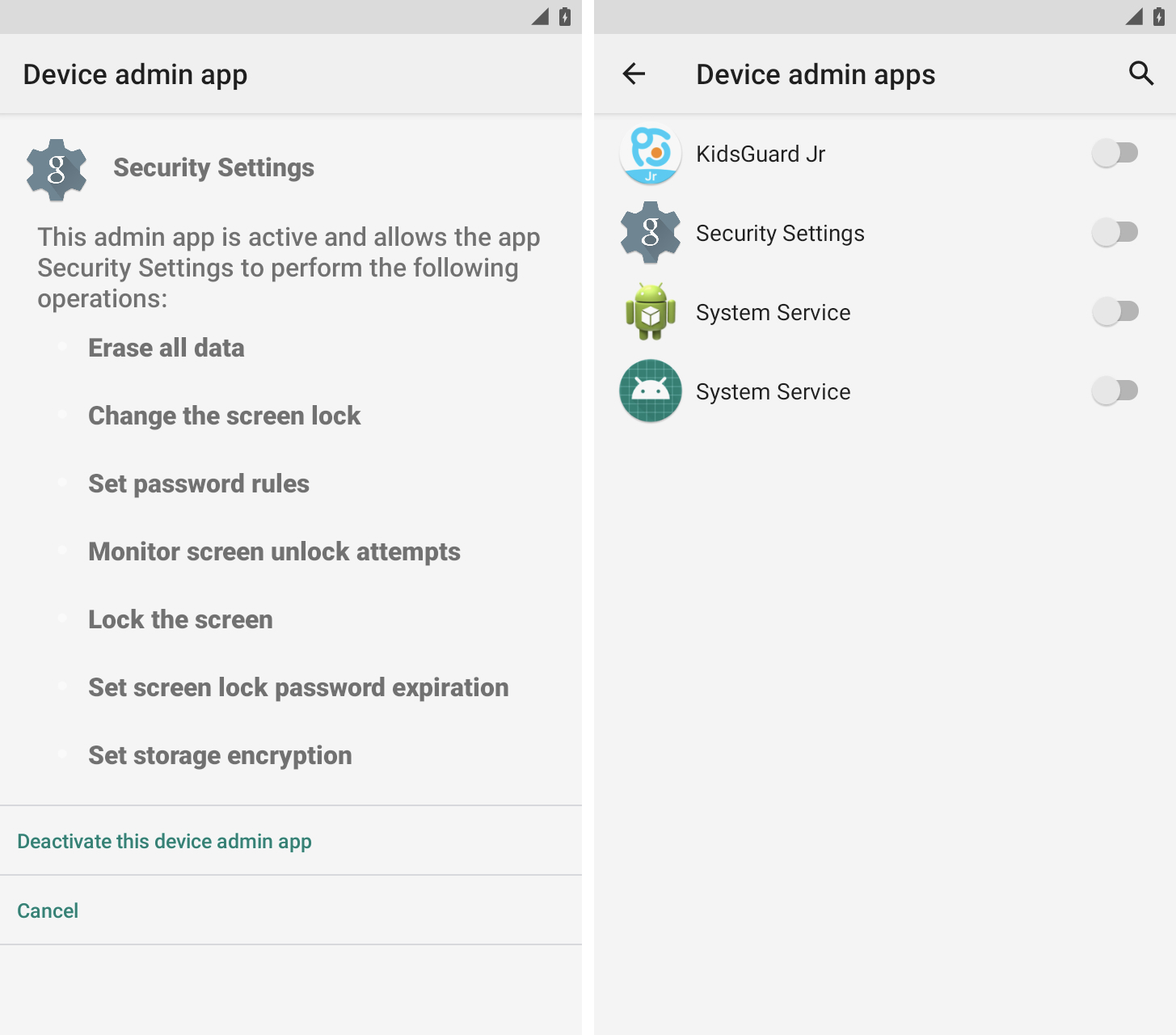

You can find the device administrator application settings to security settings.
Most people will not have a device manager app on their personal phone, so know if you see an application that you do not recognize, it is called something similar unclear and indefinite such as “System Service”, “Health” or “Admin Admin’s Admin Admin.”
Check applications for uninstall
You may not see an icon on the home screen for any of these Stalkerware applications, but they will still appear on the Android applications list.
You can see all the installed applications in Android settings. Look for applications and icons that you don’t recognize. These applications may also show that they have wide access to your calendar, call logs, camera, contacts and location data.
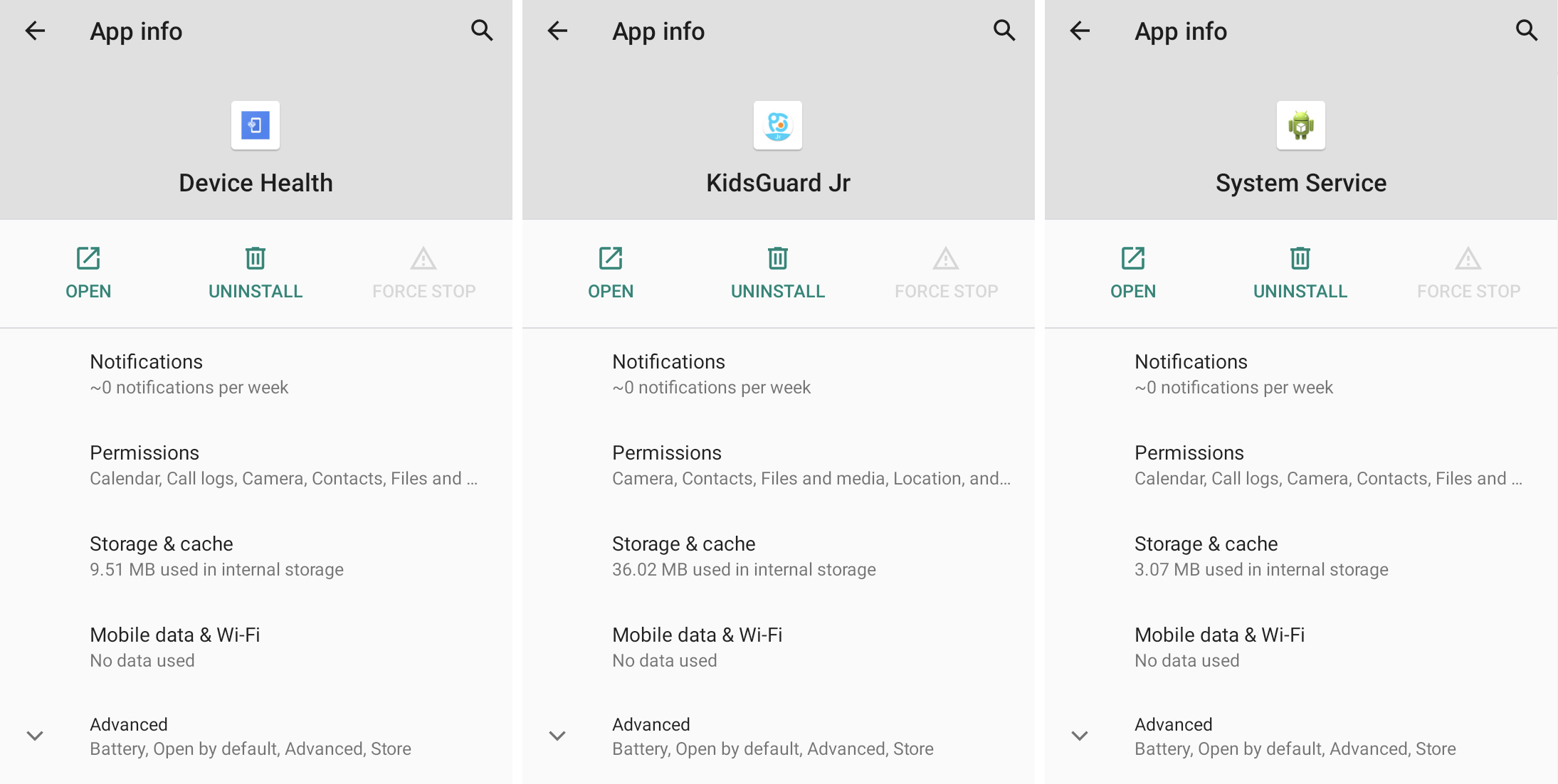

Stopping power and uninstalling a stalkerware application will probably warn the person planting the stalkerware that no longer operates.
Secure your device
If Stalkerware was planted on your phone, there is a good chance that your phone was unlocked, unprotected or that your screen lock guessed or learned. A more powerful locking password can help you protect your phone from invaders. You should also protect email and other accounts online using two -factor authentication where possible.
If you or someone you know needs help, the national telephone line for approved violence (1-800-799-7233) provides free 24/7 confidential support to victims of home abuse and violence. If you are in an emergency mode, call 911. Coalition against Stalkerware has resources if you think your phone has been violated by Spyware.