Defenders of civil liberties have long argued that “geographical attack” search warrants are unconstitutional because of their ability to ensnare completely innocent people who were nearby at the time of the crime. However, mistakes in geofencing justify applications brought before a judge can violate the privacy of many more people – in one case nearly two miles away.
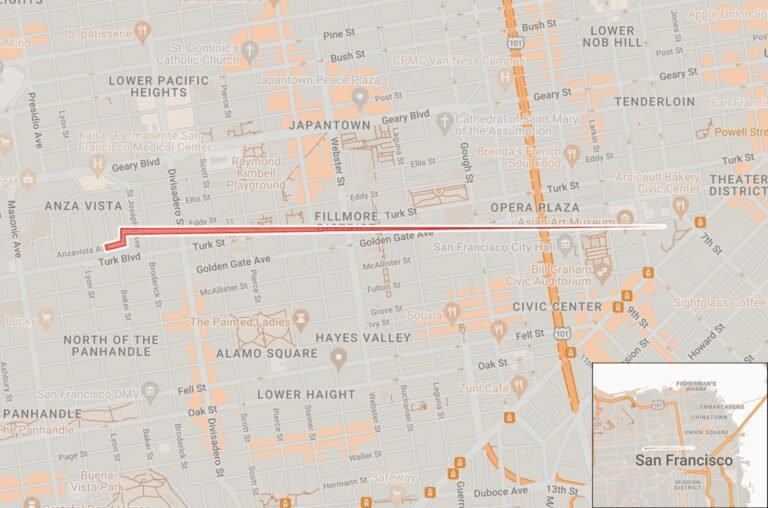
Attorneys at the ACLU of Northern California found what they called a “troubling error” in a geo-attack warrant application that “resulted in a warrant that stretched nearly two miles across San Francisco.” The error, likely caused by a typographical error, allowed the requesting law enforcement agency to capture information about anyone who entered the San Francisco area that was incorrectly noted on the search warrant.
“Many private homes were also taken in the massive sweep,” wrote ACLU staff attorney Jake Snow. a blog post about the findings.
It is not known which law enforcement agency requested the nearly two-mile long geo-trespass warrant or how long the warrant was in effect. Lawyers questioned how many other geo-trafficking warrant enforcement errors had gone through and resulted in far more data being returned by mistake.
Geofence warrants, also known as reverse location warrants, allow law enforcement agencies to seek a court order requesting data from technology companies that store vast amounts of location data on their users, such as Google, to request information about what devices have been located in a specific geographic area at a specific time, such as when and where a crime was committed. Google revealed in 2021 that geofence warrants made up about a quarter of all US legal demands it received in a few years.
ACLU lawyers reviewed thousands of geo-breach warrants filed in San Francisco Criminal Court issued over a three-year period from 2018 to mid-2021, which they say were likely only a fraction of the geo-breach warrants used in San Francisco that period. Lawyers have warned that the scope of geographic crime warrants surveillance in crowded urban areas — San Francisco is one of the most densely populated U.S. cities — often including homes and apartment buildings, busy streets and places of worship.
Attorneys said they also found a geographic crime warrant that included four places of worship on a few streets in San Francisco’s Bret Harte neighborhood, allowing police to determine “where you were and who you were with” during the warrant’s validity. .
Another geographic attack warrant in a three-block area of downtown San Francisco arrested anyone at the Le Méridien Hotel or three nearby banks, even though they had no connection to the alleged criminal wanted in the warrant. A review of the area by TechCrunch shows that the geofence area also includes the headquarters of software giant Oracle and several busy pubs and restaurants.
“Whether you were in your hotel room or grabbing a salad at Mixt Greens on Commercial Street — completely unrelated to any criminal activity — your location information may well have been shared with the police,” the ACLU’s Snow wrote.
The attorneys’ findings also showed that the geo-trespass warrants disproportionately targeted some San Francisco neighborhoods more than others, particularly immigrant-heavy areas like Portola.
Google said in December that it would begin storing users’ location data on their devices, effectively ending its ability to respond to geographic protection warrants, forcing law enforcement agencies to seek the data directly from device owners. Other tech companies that store troves of user location data — like Uber, Microsoft and Yahoo (which owns TechCrunch) — have been known to get geofence warrants.
Courts remain divided on whether geo-attack warrants comply with Fourth Amendment protections against unreasonable searches and seizures, with a potential legal challenge likely to end up before the US Supreme Court.